20160220 Rough time¶
I am getting very close to releasing the next version of Ntimed-client, and as part of my quality control, I’m in the “eat my own dogfood” phase.
Yesterday I went to Copenhagen to visit my daughter, and exploited the one hour train-ride to give Ntimed-client a rough time.
By international standards Denmark has pretty good mobile data coverage, but it is far from perfect.
One particular bad spot on this particular route is the KORSA VOR-DME transmitter which I only happen to know about because I wrote the software that keeps an eye on it for the Danish ATC.
KORSA is located 550 meter from the railroad tracks and comes with a 3km zoning restriction on anything taller then 10 meters, ie: mobile towers, and a 15km exclusion zone for windmills.
Here is how SmokePing saw the part of the trip where my VPN managed to keep connected:
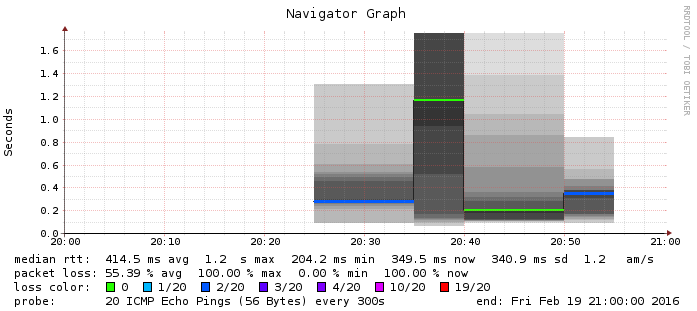
First the data shows how the HTTPStime code works:
The grey bars are the durations of each individual HTTPS request-response transaction, and the red bar is the much smaller combined window, resulting from the careful timing of when requests are sent.
Here then is HTTPStime during the full train ride:
Even under such hostile network conditions, HTTPStime manages to hold the window below half a second.
Here then are the interesting bit: How does the NTP packet results fare against the HTTPStime limiting windows:
Not too shabby it seems.
Here for comparison is the same situation from my lab:
Looks like it’s going to work.
phk
